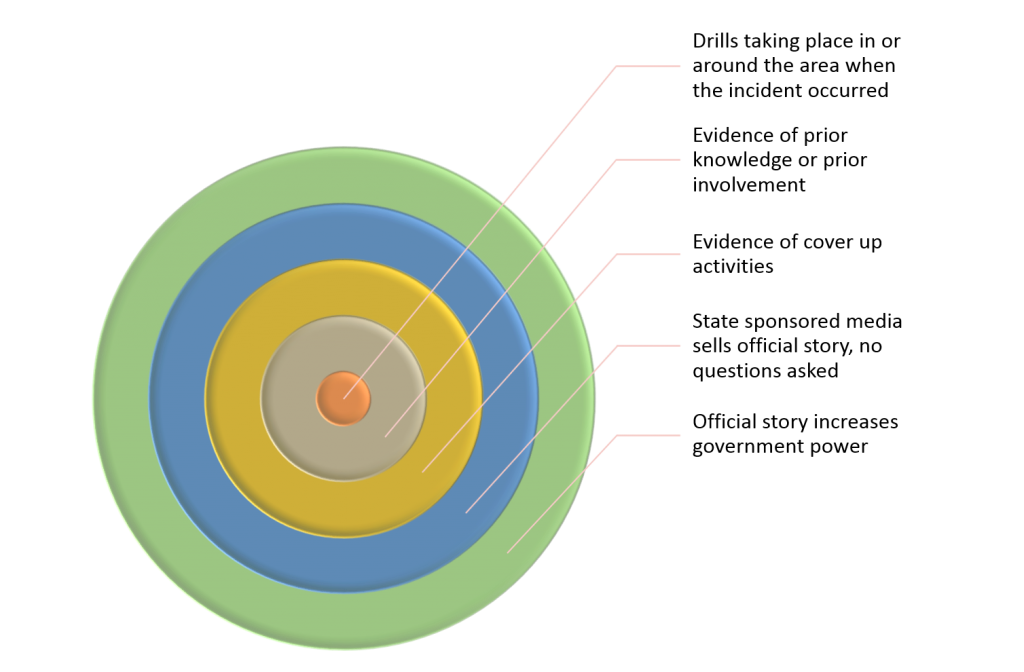
In this post we’ll apply the analysis discussed in part one to what is open source intelligence about Project Souvenir with the goal to decipher if this should be investigated officially based on the evidence that it may be a false flag operation carried out by elements within the national security establishment.
Sting vs. Inside Job
Many will claim Project Souvenir is a sting operation and that such an operation is not a false flag. Sting operations are just a few steps removed from entrapment and ultimately sit on the spectrum of inside jobs. The security establishment likes to sucker people into shades of grey. How about we don’t embark down the slippery slope that leads to full on corruption? There’s a reason countries like Sweden do not allow stings. They are fraught with ethical concerns. In this author’s opinion calling it a sting operation does nothing to deter me from the fact it is ultimately an inside job / false flag operation. It is too easy to coerce some dumb or drugged up patsy into some illegal activity and use them as a scapegoat or cover!
Cui bono? (To whose benefit?)
Whether staged or not, it is indisputable that the agencies and departments whose programs and funding will be legitimized and/or boosted from security breaches and terrorism have a clear benefit and thus a motive to potentially create, aid and puff up threats and incidents. With Project Souvenir we see the following entities and programs taking benefit:
- RCMP
- CSIS
- Canadian Border Protection Agency (CBP)
- National Security Information Network
- Integrated National Security Enforcement Team (INSET).
- War on Terror
- Domestic surveillance
- In general, government authority
Following are five primary examples of grandstanding, posturing and directing of benefit from Project Souvenir by people in the government:
1. B.C. Premier Christy Clark took opportunity to puff up the threat:
“My suspicion is they wanted to cause as much damage as they possibly could, because they want to be able to take control of our streets, our cities, our institutions, and we will not allow that.”
We also see general tugging at the heart strings of Canadian patriotism with Clark praising the work of police investigators saying that terrorists
“will not succeed in tearing down the values that make this country strong”.
Analysis: This reminds me of post 9/11, Bush-era War on Terror rhetoric and it certainly is a continuation of the War on Terror narrative to say the least. They hate our freedoms and our democracy everyone… let’s stand together in support of the great leadership of our “officials” and trust blindly those who operate under cover of secrecy courtesy of public funding. As well, we should not forget that John Nuttall and Amanda Korody are alleged culprits at this stage and have not been convicted! I find it incredible that an high ranking public servant can publicly speak as if the guilty verdict has already been served. If Nuttall and Korody are not sentenced they should certainly launch law suits at key talking heads that have clearly forgotten the common law principle of innocent until proven guilty in a court of law.
2. Reporting in the Economist a day following the RCMP briefing said:
So far there has not been a large-scale attack on Canadian soil. But the latest incident might jolt federal authorities into reversing some planned cuts to the police and security services.
Analysis: More funding for the guys to conduct more stings.
3. As we saw earlier, Vic Toews called for applause of the national security joint task force (INSET), as follows:
The success of this operation was due to the close collaboration of our security and law enforcement agencies, including CSIS [Canadian Security Intelligence Service]. I would like to applaud the RCMP-led Integrated National Security Enforcement Teams — known as INSET — and all of the partners for their outstanding work on this investigation.”
Analysis: Legitimizing domestic operation of intelligence agencies, domestic surveillance, and the duty of national security operations. It also paves the way for destructive militarization of law enforcement.
4. Repeatedly, the assertion was made in the RCMP briefing that the alleged bombing was inspired by al-Qaeda. But at the same time stating al-Qaeda inspiration they further noted there were no “international linkages” and the two alleged culprits were “self-radicalized”. However, don’t forget, it’s an al-Qaeda inspired plot. Doublethink anyone?
Analysis: Force fitting the War on Terror narrative, re-emphasizing the omniscient threat of al-Qaeda.
5. Finally, RCMP Assistant Commissioner James Malizia uses the crisis to promote a homeland security program, saying,
“It is very important that Canadians remain vigilant. We urge the public to bring any suspicious activities to the RCMP’s attention through our national security information network.”
Analysis: If you see something, say something… provided it fits our narrative. This citizen spy atmosphere, as if taken from the Stasi or Nazi SS, must be a product of the “harmonized” homeland security initiatives that have been agreed to in secret between Canada and the U.S. “Beyond the border vision” anyone?
Consider this motive for RCMP and Public Safety
Before we look further at stronger indicators of potential corruption, let’s examine a final point on cui bono: The RCMP’s stated target for the number of times it intends on disrupting “terrorist criminal activities”. The RCMP effectively has a quota of six (6) times where they are expected to prevent terrorism in Canada in a specified period. You can see it on page 19 of the RCMP’s Report on Plans and Priorities 2013-14. You might ask: What if there aren’t incidents to disrupt? Well, clearly, we are back to having a clear motive for staging incidents and/or entrapping dumbies to achieve a certain benefit. As described in the document: 6 is the “Number of disruptions, through law enforcement actions, to the ability of a group(s) and/or an individual(s) to carry out terrorist criminal activity, or other criminal activity, that may pose a threat to national security in Canada and abroad”.
Consider the public relations opportunity
Just another point to consider, the RCMP press briefing and B.C. Premier Christy Clark’s public announcements related to Project Souvenir occurred on July 2, 2013, a day after Canada Day, Canada’s national celebration of its (supposed) independence. On the heels of our most patriotic day, Clark’s rhetoric has an increased appeal.
Prior knowledge
Let us now turn our focus to evidence of prior knowledge. For this, we find obvious leads in the RCMP’s own admissions during their July 2nd press briefing where Project Souvenir was first made public.
“The suspects were committed to acts of violence and discussed a wide variety of targets and techniques,” said Assistant Commissioner Wayne Rideout.
RCMP Assistant Commissioner James Malizia had other indicators in his written statement:
“These charges are the result of an RCMP investigation named Project Souvenir, which was launched in February 2013, based on information received from the Canadian Security Intelligence Service. These individuals were inspired by al-Qaeda ideology. Our investigation demonstrated that this was a domestic threat without international linkages. I want to reassure our citizens that at all times during the investigation our primary focus was the safety and protection of the public. While the RCMP believes that this threat was real, at no time was the security of the public at risk. These arrests are another example of the effectiveness of our Integrated National Security Enforcement Team who work tenaciously to prevent this plan from being carried out. We detected the threat early and disrupted it. On behalf of the RCMP, I want to express our appreciation to CSIS and all our partners for their tremendous support throughout this investigation.
Specific details are not public at this time, but it is clear that Nuttall and Korody were under surveillance. When did surveillance begin? I think it is fair to say that likely on or sometime before the February 2013 founding of the joint task force operation known as Project Souvenir, six months prior to the arrests, is when continual surveillance most likely began. That’s a long time to have prior knowledge.
I also find it interesting that CSIS is the source on this entire investigation. We just have to take the word of the guys who operate under total cover of secrecy and have a history of linkages to international secret societies, international criminal operations and have no real accountability to the public or elected representatives. I’d love to investigate whether dark elements within or tied to CSIS promoted Nuttall and Korody out of some MK-ULTRA program and then tipped RCMP off to do their thing. Evidence of handlers and mind control on Nuttall and Korody would support this working hypothesis. (In part three of this series, we’ll look closer at Nuttall and Korody).
According to the RCMP’s narrative, let’s move on to see what they did with their prior knowledge.
Prior involvement
If there is evidence that folks from the intelligence community or law enforcement special operations units were involved in any aspect, from funding, training, aiding, cajoling, or otherwise participating, then you can start placing your bets on this being a false flag operation.
As reported by the Economist:
Investigators had apparently become close enough to the plot to render the bombs harmless.
This is somewhat eluded to in a statement by RCMP Assistant Commissioner James Malizia, as follows:
“At no time was the security of the public at risk,” said Malizia. “We detected the threat early and disrupted it.”
They disrupted it? Well, skeptics of my analysis might say that disrupting it means they stopped it from happening when they presumably jumped out of the bushes to arrest the alleged bombers. However, the RCMP confidently and clearly says that there was no security risk to the public, at any time! The only way for this to be true is if undercover agents (agent provocateurs) were engaged with the improvised explosive device (IED) in advance of the arrest. Assistant Commissioner Wayne Rideout clarifies for us with a more definitive statement:
“These devices were completely under our control, they were inert, and at no time represented a threat to public safety.”
Incredible! “Completely under our control…”. In order for this to be true, an undercover officer would have indeed had to have been hands on with the IED, possibly supplying it in the first place, and indeed quite close to Nuttall and Korody to gain their trust to participate in the plot. How else could the RCMP be in complete control of the device and know it was inert?
During the July 2 press briefing, Mr. Rideout was asked about the techniques employed by undercover officers, specifically if they had acted as collaborators in the plot. Evasively Rideout said,
“I’m not prepared to go into the details of how we were able to disrupt and assure public safety, but there are a vast number of resources and specialty groups that are available to us. We employed most of them.”
Wow. Tenacious. Professionals. Specialists. High-end and sophisticated. That’s the public relations image being projected here, but any thinking individual smells a rat and now has more questions than answers.
Conclusion
Project Souvenir has all the markings of a false flag operation. We have strong evidence (of prior knowledge and involvement) telling us there is a deeper back story here. We also have multiple and clear motives for this to be staged. The suspects for staging such an incident have a history of employing such tactics and they are also deeply entwined with international counterparts that do as well. And we also have to factor in that the entities involved have the ability to operate with the cover of national security. As history has proven, secrecy breeds corruption.
If there is evidence of drills for a similar incident being run by local law enforcement during the time of this incident, then we have all the tell-tale signs of a false flag operation.
With deceptive tactics such as false flag operations, patsies and provocateurs regularly used by law enforcement, the intelligence community and black ops, we must not be quick to agree with the conclusions we’re being given in press briefings or shallow news reporting. We must remain healthy skeptics of government and we must investigate agencies that have a history of deception and law breaking. At this stage, I think it is obvious that the official story from the RCMP briefing must be transparently investigated by an independent third party.
In part three, we will take a closer look at Nuttall and Korody, the alleged bombers, and explore the issue of them playing patsy to this “operation”.