On July 2nd, 2013 the Royal Canadian Mounted Police (RCMP) held a press conference to announce their success in thwarting an alleged homegrown terrorist attack that, according to their report, was to target the provincial legislature in British Columbia on Canada Day with an improvised explosive device (IED) made of pressure cookers. In the RCMP’s press briefing, they revealed that the proactive arrest of two alleged culprits came as a result of a 6-month joint task force investigation named Project Souvenir.
Following the press briefing, Minister of Public Safety (at the time) Vic Toews heralded Project Souvenir a successful “operation”. “The success of this operation was due to the close collaboration of our security and law enforcement agencies, including CSIS [Canadian Security Intelligence Service],” he said. “I would like to applaud the RCMP-led Integrated National Security Enforcement Teams — known as INSET — and all of the partners for their outstanding work on this investigation.” The “partners” in question were named as RCMP, CSIS and Canadian Border Protection Agency (CBP), but it is likely that Communication Security Establishment (CSE) (Canada’s NSA equivalent) would have also been involved.
From July 2nd to July 4th major news outlets like the CBC, BBC, the Economist and others published articles with consistent talking points, which were mostly parroted from the RCMP press briefing. Across the board, news reporting supported the RCMP statements without question. Mainstream news reporting also went on to mention the other recent alleged terrorist acts by Canadians that were intercepted by “authorities”, as if to paint the picture that this is a growing trend in Canada.
At this point, I suppose we should all be happy. Perhaps we should even start to get comfortable with the government monitoring our communications because that’s how this rising threat of terrorism is going to be combatted, right?
The official narrative leans us towards the conclusion that the federal government is doing its job; that the national security apparatus is efficient; that sting operations are just and a great tactic for public safety. I suppose any other line of thinking would be heretical and nothing more than a conspiracy theory.
Unfortunately, Project Souvenir stinks for several obvious reasons which will be discussed in this series. It stinks of entrapment; a type of false flag operation; a self-inflicted wound.
In this post, part one of a series, we will establish an understanding of a false flag operation and look at how security incidents in general might be analyzed to decipher the potential of a false flag. Follow-on posts in this series will provide analysis of Project Souvenir in more specific detail.
What is a False Flag?
Let’s take a quick look at the definition, characteristics and reasons of a false flag operation.
Definition
Simply put, a false flag operation is an inside job with the design to place blame on a certain entity for purposes of some gain. False flag is a military term that originated in naval warfare, and the tactic has long been used in both hot war and peace-time clandestine operations.
Characteristics
There is a spectrum of false flags. Involvement can be extremely minimal, such as taking actions certain to create conditions for another party to react a certain way, thus indirectly generating an event to be used for gain. The far other end of the spectrum is the direct involvement and carrying out of an operation while posing as the entity to be blamed for the event.
Reasons
Rooted in Hegelian dialectic, a false flag operation is essentially a crisis to be leveraged for the realization of some goal. Undoubtedly, a real crisis can be leveraged for political gain; however, a staged or created crisis is useful just the same provided the true perpetrators are not exposed and the event is understood to be manufactured.
When a crisis occurs, with the pain fresh in the mind, people are malleable; more willing to sacrifice something that they believe will be a solution to the crisis. Think about it, because we’ve all been subject to false flags – even historical crisis that occurred before our birth can have an impact on our ideological perspectives and beliefs.
Historical examples
There are dozens of examples of false flags in modern history carried out by American, British, German, Japanese and other governments. Operation Ajax has been discussed on this site. Operation Northwoods is another great example. The Gulf of Tonkin incident is another.
In Nazi Germany, Nazi leadership employed false flag operations as a precursor to advancing a police state over the domestic population and as a means to building public support for military aggression. For instance, in 1939, German public support for war on Poland was manufactured by dressing prisoners from Nazi concentration camps in German soldier uniforms, then having the Gestapo gun them down, followed by propaganda that portrayed them as German soldiers murdered by Polish aggressors. The scandal is known as the Gleiwitz incident and is a great example of how the ruling class requires consent from the sheep-like public.
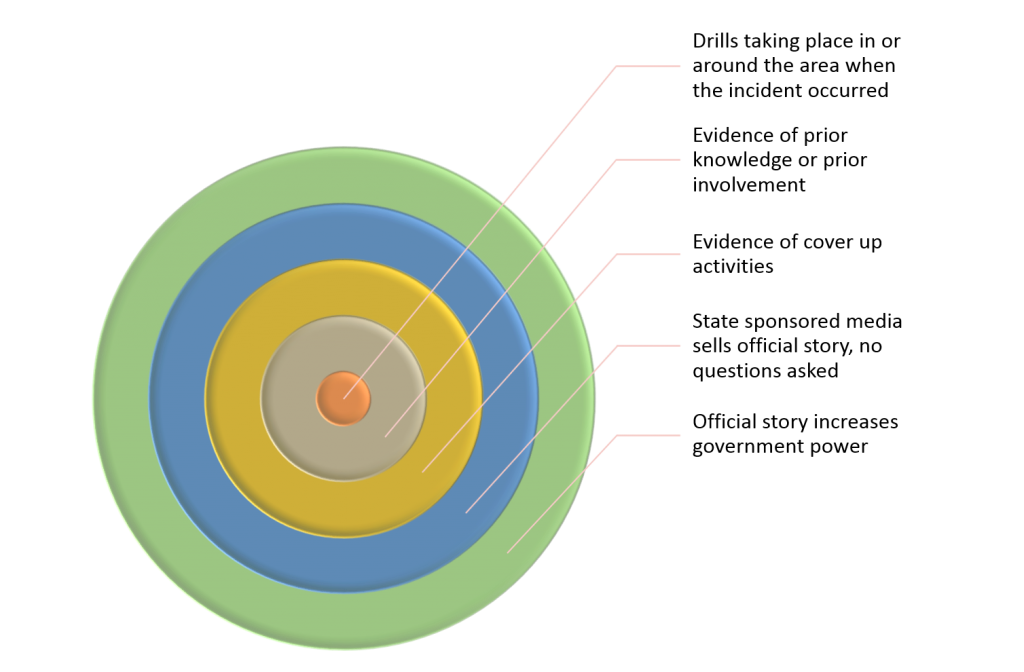
Common Indicators of a False Flag Operation
Following is a brief overview of the most common and obvious indicators that an event might be staged. Look for these things and these questions the next time a security incident is presented to you.
- The official story increases government power – Does the incident work as a catalyst or justification for new programs? Is it being positioned for use as a reason to increase funding for a program or department? Does it legitimize programs that are unpopular, under attack and would represent a significant loss of government power if overturned?
- The news media carries a common meme, avoids asking tough questions – Are the major news outlets failing to look at key evidence or ask tough and obvious questions? Are there logical fallacies that if discussed would oppose the government’s official storyline? When the incident first occurred, were significant leads reported that never again received any coverage?
- There is evidence of cover up activities – Are whistleblowers speaking out? Are people close to the issue saying something stinks and then these same people go quiet? Are public requests for information ignored or stonewalled? Has key evidence been destroyed? Where real corruption has occurred and the truth starts to come out, things like evidence destruction, intimidation tactics and mysterious suicides or disappearances will usually be observed.
- There is evidence of prior knowledge – If the “authorities” knew certain details in advance then we have to ask: Was it not stopped because of incompetence? Negligence? Evidence of prior knowledge can be an indicator that a stand down occurred, which would mean complicacy and thus an inside job at some level. More than a stand down, prior knowledge can also indicate that certain internal elements were involved in carrying out the incident.
- Evidence of prior involvement – Includes any type of assistance, facilitation or interaction in the event. If this is determined, then an investigation must be carried out by an independent and transparent body. Were the patsies trained by those responding? Was the device controlled by those responding? Were the attackers transported by those responding?
- There were drills being conducted at the same time the incident occurred – Through compartmentalization, an inside job will typically be conducted under the cover of drills. In other words, useful idiot elements within the department or community are involved in executing what appear to be standard drills. During the exercise(s), corrupt elements participating in or alongside the drill will conduct or facilitate the real attack. Those carrying out the drills have no idea that they are effectively providing cover for a false flag operation.
The following diagram depicts the indicators that a false flag operation is likely:
Conclusion
We need to question the official narrative on Project Souvenir and think critically about the information that is provided to us by those that stand to gain. Not every security incident is an insider conspiracy; however, more often than not such “operations” as Project Souvenir are corrupt and will be used for political gain.
In the next post we will apply our analysis against what is known about Project Souvenir to ask the question: Are elements within the Canadian government conducting a false flag operation?

I would rather see a false flag then CSIS knowing about the LAX bombing 9 years before it happened under the “Liberal” reign. Don’t be so naïve….there is a long distinguished list of Liberals who have attended Al Qaeda fundraisers in this nation….since the late 80’s.